Bring your own device (BYOD) policies are increasingly popular among businesses that want to allow employees to select or upgrade their own devices, but these policies can also create security concerns. Researchers from Nanyang Technological University in Singapore believe a new authentication scheme employing facial biohashing and a physical unclonable function, or PUF, for personal devices could provide greater BYOD security.
BYOD policies allow employees to use more sophisticated electronic devices – like computers and cell phones – than companies can provide. However, the trend can also make organizational data and systems more vulnerable to breaches, since companies have little control over their employees’ individual devices.
Current authentication schemes for employee devices either authenticate the user or the device. To protect company data, authentication schemes need to be able to authorize the user and ensure the device being used is trusted by the company’s network.
Biohashing is the technique of collecting raw biometric features and then transforming those features into templates to prevent privacy invasion and allow users to be revoked. To authenticate a user, a biohashing system takes the user’s facial features and then compares those features against randomly projected facial templates stored in the system.
Biohashing systems are vulnerable because people assume the randomization of the system’s projection matrix can never be compromised, shared or cloned. However, all the data used to create the facial templates in the system can be easily accessed by the hackers.
The Nanyang Technological University team was able to solve this issue by combining biohashing with a physical unclonable function (PUF) for personal devices that is derived from a CMOS image sensor.
“PUF serves as a unique ‘device fingerprint’ as it exploits the unpredictable fabrication process variances of integrated circuits in a device,” said Chip-Hong Chang, associate professor at the School of Electrical and Electronic Engineering of Nanyang Technological University. “A PUF is a circuit that generates a unique digital code for these manufacturing differences to identify an authorized device.”
In the researchers’ system, personal devices are embedded with a PUF, preferably built directly from or around the pixel array of the image sensor. Authorized users and verified devices are enrolled in the system with biohashing. When these users try to access a company server connected to the system, the system requires authentication from the user and the device.
As seen in the diagram below, users must take a picture with their personal device, while the PUF generates a device key to create the random projection matrix for biohashing. Facial features and the device key are unified by biohashing to create the transformed template for authentication. If neither the user nor the device meets the designated threshold for verification, the system will not grant access to the server.
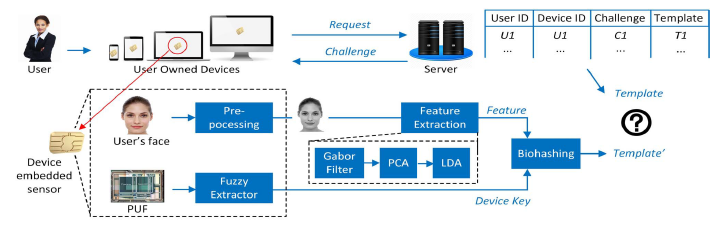
Figure 1: Verification scheme using the proposed biohashing-based user device PUF.
To test their system, the researchers conducted simulations using two databases of facial images with one database of 400 faces as the authorized users, and the other database of 15 faces as impostors. The researchers also tested the PUF by simulating the responses generated from a CMOS image sensor based PUF.
The researchers evaluated the hamming distance – the number of substitutions required to change one template into another – between the obtained fake templates with the enrolled templates for their simulations. As seen in the graphs below, they found their system had a low false accept rate regardless of the user, device or challenge (the randomization of facial features projected).
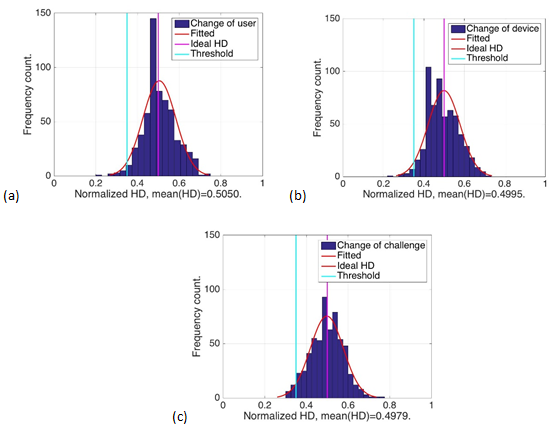
Figure 2: Discriminability against: (a) Case 1: Different user, same device, same challenge. (b) Case 2: Same user, different device, different challenge. (c) Case 3: Same user, same device, different challenge.
To advance their system, the team is looking to incorporate other biometric features such as fingerprints, vocals, iris and gait. Additionally, they will look to improve the security of their system by upgrading from the CMOS sensor based PUF, as there are stronger PUF alternatives.
IEEE Spectrum reports companies like Adobe and Google are exploring software that can fabricate video or audio clips. A biohashing system with improved authentication methods, like the one developed by these researchers, could better protect companies as new technology makes other biometric systems vulnerable to fake video or images.
For more information on biohashing, visit the IEEE Xplore Digital Library.





