As the Internet of Things (IoT) steps out of its infancy into full maturity, the question of how to manage billions of devices worldwide–from fitness trackers and home energy systems to autonomous vehicles and medical devices–is becoming critically important. According to Gartner, over 20 billion IoT devices will be installed for consumer and commercial applications by 2020. In both cases, these devices will have their own digital identity and manage user data, all while maintaining security and privacy. Tampering with these devices is not just a nuisance–it could be life threatening in some cases.
While access management technologies do exist in the IoT, they are based on centralized models that bring technical limitations on the global scale. To address this issue, a team at the University of Helsinki proposed a new architecture for arbitrating roles and permissions in the IoT.
“Our architecture provides a decentralized management system connected to a geographically distributed sensor network,” explained Oscar Novo. “The solution is based on blockchain technology, which eliminates the bottleneck effect caused by a centralized system, and allows new IoT devices to join easily.”
As IoT devices are unable to store blockchain information, the architecture employs management hub nodes, which request information from the blockchain on behalf of the IoT devices. Entities called “managers” are responsible for implementing permissions for a set of IoT devices and interact with a smart contract to determine this access control policy without the need for human interaction.
A visual representation of the architecture and its components can be seen in Figure 1 below.
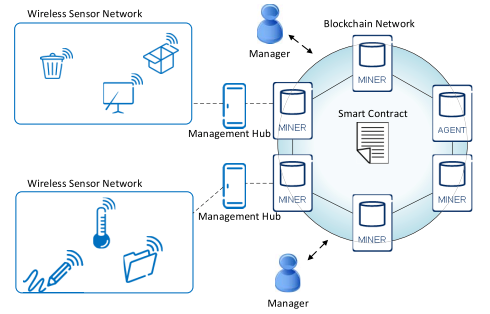
Figure 1: Decentralized Access Control System Architecture
“Our architecture allows IoT devices to connect to one another on a large scale without the need for human moderation,” Oscar explained. “By decentralizing this process we hope to streamline the use of IoT devices, as the information they gather will no longer be held up and processed in specific geographic locations.”
In order to test this novel approach, two experiments were performed to measure the performance of the architecture–one to evaluate the performance of the management hub independently and a second to evaluate the performance of an IoT device connected to a management hub node.
The first scenario (called management hub in figure 2) shows how the management hub achieves a steady throughput of 950 requests per second with ten to one thousand concurrent clients, before slowly declining as the number of clients rises (shown by the number of timeouts). The second scenario (called IoT device in the figure) achieves a steady throughput at 500 requests per second during all the tests. In this scenario, all the concurrent clients request the resource information from a single IoT device.
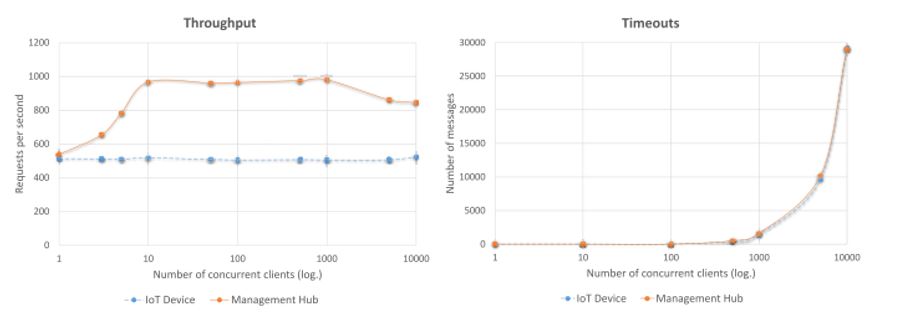
Figure 2: Results from Architecture Evaluation
While the team viewed these results as generally favorable, the architecture did suffer from waiting for the blockchain network to issue access control information. Still, the management hub performed well with up to 1,000 concurrent clients without excessive timeouts. Moving forward, the team will continue to improve the architecture’s security, as well as its integration capabilities.
The goal of Novo and his team was to provide a generic, scalable, and easy-to-manage access control system for the IoT. Their study showed their architecture is able to adapt to various IoT scenarios, confirming that blockchain technology can embrace the IoT at its fullest. As IoT devices become more prevalent, this network management solution may prove valuable in keeping IoT data secure and allowing users to quickly access a geographically dispersed IoT network.
For more information on IoT visit the IEEE Xplore Digital Library.





