As the digitization of critical infrastructure continues to accelerate across industries, cybersecurity has become an essential topic in the global discussion. Cyber-physical systems (CPS) integrate physical systems in the real world and control software in computing systems. According to researchers, the introduction of networking technologies in CPS has substantial advantages in system efficiency, scalability, and maintenance. However, CPS is vulnerable to malicious attacks on the network. In a recent article published in IEEE Communications Surveys & Tutorials, authors conduct a comprehensive review of the literature on threats to CPS and resilient CPS design strategies. The review's primary focus is to ensure the stability of physical systems under cyber-physical attacks.
Networked Cyber-Physical Systems and Attacks
The authors begin the article by providing a basic knowledge of control theory for general network engineers to understand the behavior of the physical systems of CPS. The attention is focused on the three components for controlling the physical systems: the physical system, the state estimator, and the controller. Next, the authors introduce a hierarchical CPS structure consisting of the physical, network, and application layers.
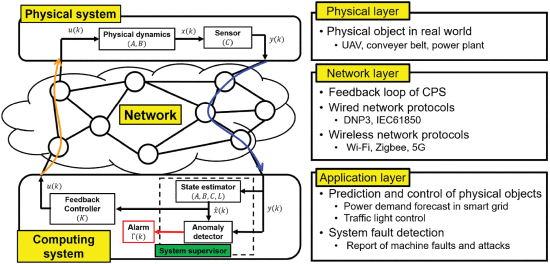
Structure of a networked control system.
Cyber-physical attacks destabilize physical systems—in the article, the authors cataloged attacks using three perspectives: attack space, location, and stealthiness. The cyber-physical attack space represents the characteristics of cyber-physical attacks: system knowledge, disclosure, and disruption resources. The attack location is a type of data modification manipulated by the attacker on the network. The attacker can exploit two types of data: sensor measurements and control input signals.
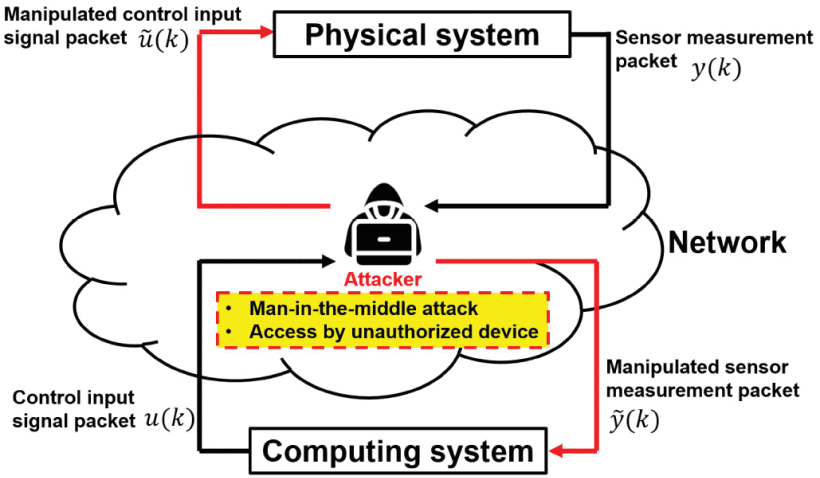
Man-in-the-middle attack for cyber-physical attack implementation; Cyber-physical attack location.
Finally, stealthiness refers to an attack not detected by an anomaly detector based on the physical system model. A cyber-physical attack with stealthiness can destroy the physical system while avoiding an attack detection alarm on the anomaly detector. The article systematically analyzes the most common cyber-physical attacks, including the DoS attack, the replay attack, the zero-dynamics attack, the pole-dynamics attack, and the covert attack.
Resilient CPS Approaches
The authors outline detection strategies, focusing on three types of anomaly detection strategies: model-based detection, statistical detection, and learning-based detection. Security of CPS includes attack detection, handling, and mitigation to ensure the stability of the physical systems under cyber-physical attacks. To that purpose, resilient CPS design approaches in terms of control, network, and data-driven strategies against system faults and cyber-physical attacks are covered.
To highlight the effect of resilient CPS design, the authors provide two examples of cyber-physical system recovery: inverted pendulum recovery against a DoS attack and emergency braking on a CBTC system against a controller attack. The first example provides a resilient CPS design from a control-theoretical viewpoint. The second example offers a resilient CPS design in a realistic scenario.
Future Research Directions
Malicious attackers can compromise cyber-physical systems causing significant damage to physical equipment and human casualties. It is necessary to analyze and detect cyber-physical attacks, designing CPS with reliability and resiliency to ensure the safety of CPS from cyber-physical attacks. Resilient CPS aims to guarantee the physical systems' stability under various cyber-physical attacks and system faults. To advance the resiliency of CPS, the authors suggest three future research directions: resilience for control, resource management of security mechanisms, and resilient CPS architecture.
View the full-text article on IEEE Xplore. Full article available with purchase or subscription. Contact us to see if your organization qualifies for a free trial.