Internet-of-Things (IoT) applications involve many interconnected devices performing predefined tasks. Sophisticated cyber-attacks on IoT applications are often launched when malicious entities gather enough information about the characteristics and operations of the network and the connected devices. Different security mechanisms are put in place to protect the information exchange between the devices. In most cases, when the IoT applications are deployed, a static network topology and configuration are used.
The proposed solution to this security problem is to switch from a static network configuration to a dynamic one. In a paper presented at the 2023 International Conference on the Design of Reliable Communication Networks (DRCN), researchers proposed MTDIoT. This moving target defense solution changes the network configuration dynamically over time (or upon specific events), making it hard for an external attacker to target specific devices and services. The proposed solution can isolate compromised nodes from updated network configurations, has minimal compute requirements, and introduces no burdens or limitations—making it ideal for IoT deployment.
This approach, called Moving Target Defense, is based on the idea that if the defending infrastructure is constantly shifting, it becomes much more challenging for a malicious entity to discover and exploit vulnerabilities or deploy and successfully execute attacks. According to the researchers, the system is designed to cooperate with other commonly used security components (such as Intrusion Detection Systems or Security Assurance Platforms), which can act as the triggering sources for applying new configurations.
MTDIoT Design
The focus of MTDIoT primarily falls on the dynamic network domain. However, the exponential rise of IoT applications that deal with sensitive information forces the consideration of data encryption schemes, especially for data transmissions in channels. As noted by the authors, the MTDIoT system must be able to include techniques that properly consider encryption schemes as well (dynamic data domain).
The proposed MTDIoT solution targets IoT deployments and considers a network configuration that follows a tree structure. Leaf nodes are occupied mainly by simple devices (sensors, cameras, actuators, etc.) that communicate with edge nodes. These leaf and edge nodes constitute the most important part of the overall infrastructure that the MTD scheme must protect.
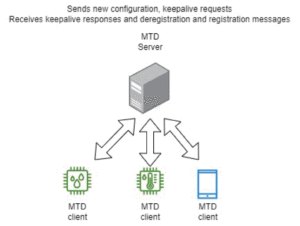
MTDIoT architecture
Considering the design requirements, the MTDIoT application is built as a client-server system. A central node located at the network's edge generates new configurations and propagates this information to all connected leaf nodes. This way, all the computational complexity is gathered on capable nodes, and resource-constrained devices need only execute simple network configuration tasks of their own communication interfaces.
MTDIoT Implementation
The MTDIoT server is installed in a computationally capable edge node, and it is responsible for managing all the clients, handling events like warnings originating from external security components, and generating new configurations. Because of the dynamic nature of IoT applications, as noted by the authors, leaf nodes are expected to have intermittent connections to the rest of the system. MTDIoT clients dispatch specific messages about their liveliness state that the server uses to draft an updated image of the overall network.
The MTD clients are responsible for managing the network configuration, maintaining an encrypted connection between each other using the routing table sent by the MTD server, and applying any changes the server sends. The MTDIoT system supports shuffling between different encryption algorithms and keys—and handles this process transparently from the application layer. An included cipher receives unencrypted data from the application running on the local device, encrypts them according to the rules specified by the MTDIoT server, and then dispatches them to other nodes. The inverse functionality is realized upon the reception of encrypted messages.
Conclusions and Future Directions
In studies, the researchers used a testbed to assess the performance overhead of the proposed approach. The initial results are promising and indicate that the solution is lightweight and does not impose a significant memory footprint or latency issues on the devices. While further testing is needed to confirm these initial findings, the researchers are optimistic about the approach's potential to meet the needs of practical applications.
Future directions for implementing MTDIoT include testing the proposed solution in real-world IoT deployments to evaluate its effectiveness in protecting against cyberattacks. Also, additional security mechanisms, such as intrusion detection and prevention systems, could be integrated into MTDIoT to enhance its overall security. Another potential direction is exploring machine learning and artificial intelligence to develop more advanced MTD schemes for IoT networks.
Interested in learning more about Cybersecurity and the Internet of Things? IEEE offers continuing education with the Cyber Security Tools for Today's Environment and the IEEE Guide to the Internet of Things (IoT) course programs to smartly implement digital tools into your organization.
Interested in acquiring full-text access to this collection for your entire organization? Request a free demo and trial subscription for your organization.





