Drones have become valuable assets for many military and civilian operations. In the last decade, these technologies have aided in military reconnaissance, search and rescue operations, and enforcing social distancing among civilians during the COVID-19 pandemic. With the advent of 5G wireless communications, more advancements and use cases are expected from drones, specifically tied to data and information gathering. However, with wider deployments come more privacy violations and security breaches for government agencies, corporations and the general public.
Researchers believe that leveraging blockchain could enhance and simplify privacy preservation associated with data collection, handling, storage and analysis in 5G-enabled drones.
5G networks have been deployed globally due to their low latency and ultra-high bandwidth and reliability capabilities. Today, 5G-enabled drones come in two forms; 5G base stations to enable and enhance terrestrial wireless communications, and 5G users in that they leverage 5G networks to perform tasks and communicate with other drones. As outlined in Figure 1, a swarm of 5G-enabled drones, coordinating and collaborating with each other can form a web of networking, computing and storage resources in the sky – valuable components for numerous scenarios across industries.
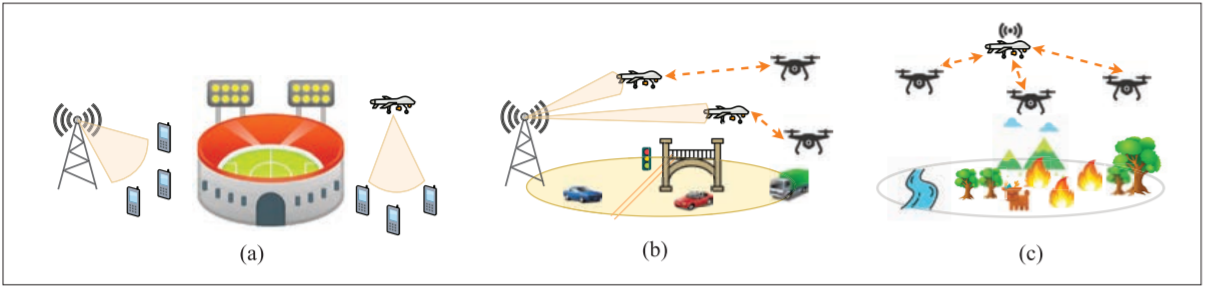
Figure 1: Three typical scenarios in 5G-enabled drone communications: a) using 5G base station drones to enhance 5G communication capacity b) using 5G user drones to draw a map in a drone-to-drone (D2D) cooperative way c) using a combination of both 5G base station drones and 5G user drones to perform search and rescue in a wildfire
“Since drones can be used as base stations or users – [such as] data collectors from the Internet of Things nodes – the type of data [that] can be collected and stored can vary widely,” said Yulei Wu with the Department of Computer Science at the University of Exeter in the United Kingdom. “Typical data types may include numerical data, ambiance sound, text, audio and video. Moreover, the storage of these data may be transient or persistent depending on the application scenario.”
With so much data being collected and analysed, the question of who can legitimately access it and how to protect its privacy comes into play. Unauthorized aerial surveillance, espionage and armed attacks are just some of the security and privacy challenges that remain an ongoing concern for many entities, until now.
Blockchain – a decentralized public ledger that contains cryptographically generated data blocks that make it difficult to hack and change information – is a viable and tamper-proof solution for government and business entities looking for secure and transparent drone operations. And it’s what the team incorporated into their solution for 5G-enabled drones. Leveraging the technology, the team’s concept aims to address identification (ID) management, data privacy and trajectory protections, and network collaboration between drones. Their solution is outlined in Figure 2.
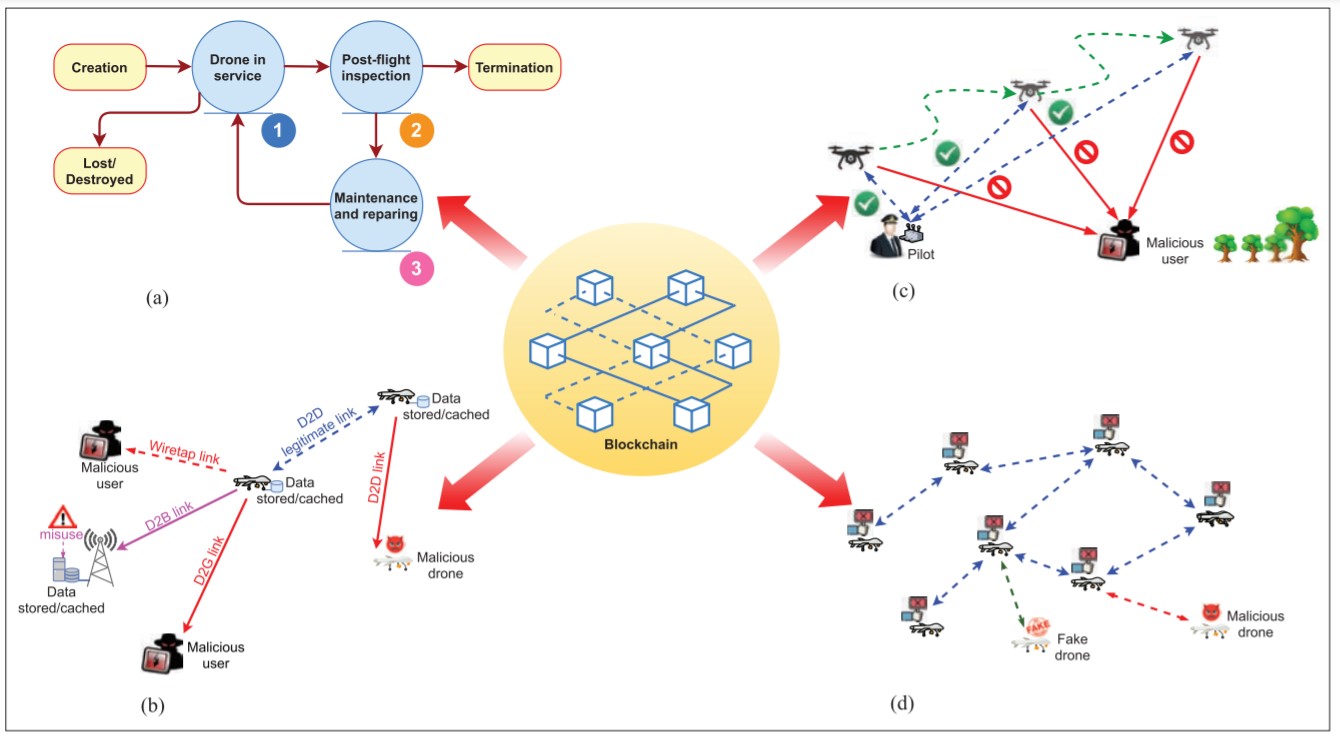
Figure 2: The team’s blockchain-based privacy preservation for drone communications: a) drone ID management b) data privacy protection c) trajectory privacy protection and d) collaboration of drone networks
Through the team’s decentralized blockchain-based system for ID management, a drone can identify and or revoke any expired ID by analyzing and tracking historical records. The consensus mechanisms in blockchain also support in determining the legitimacy of drones in order to prevent malicious attacks from occurring, such as a Sybil attack. The blockchain-based ID management system can cover the entire life cycle of a drone. Three active stages are outlined in Figure 2a.
According to Yulei, while ID management plays a critical role in drone communications, there are few studies and real-life applications today leveraging blockchain-based solutions to enhance this capability.
As for attackers intercepting and stealing data from drones, the team’s blockchain-based authentication mechanisms can determine whether an access request initiated from a drone was authorized. Blockchain-based encryption and cryptographic schemes including asymmetric encryption algorithms and homomorphic obfuscations can also be deployed to mitigate threats at the drone-to-drone (D2D), drone-to-ground (D2G) and drone-to-base-station (D2B) levels, as shown in Figure 2b.
Figure 2c outlines the potential flight vulnerabilities in 5G-enabled drone communications. Once a drone’s trajectory has been exposed, it can be tracked, intercepted and hijacked by malicious users. The stolen data can also be used to carry out other nefarious attacks. Blockchain-based authentication and access control mechanisms guarantee authorized access and protect the flight course of drones. The same solutions can be leveraged in the case where a team of drones are deployed, as illustrated in Figure 2d.
Separate, these solutions will significantly diminish privacy and security breaches, but integrated together these solutions can create a wall of protection that is almost impenetrable. Figure 3 summarizes the capabilities of the team’s blockchain-based solution.
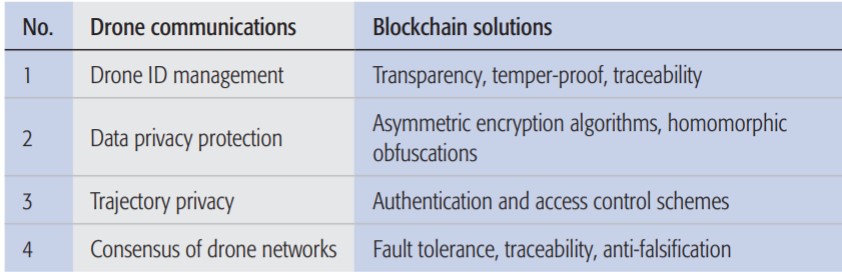
Figure 3: Summary of blockchain-based solutions in drone communications
Despite the benefits of incorporating blockchain in drone communication for privacy and security purposes, a number of open challenges remain, including regulation development and compliance enforcement. As a next step, Yulei and his team are looking to adopt forensic-by-design principles in future drone systems, where artificial intelligence (AI) agents can be used to automatically identify and collect artifacts for forensic interest. AI-driven cyber defensive systems can also be trained to identify future threats and facilitate future cyber investigations and attributions.
For more information on 5G, drones and blockchain, visit the IEEE Xplore Digital Library.





